Spectre Next Generation Flaws could potentially affect your CPU After Spectre and Meltdown bugs shook the computing world, there are
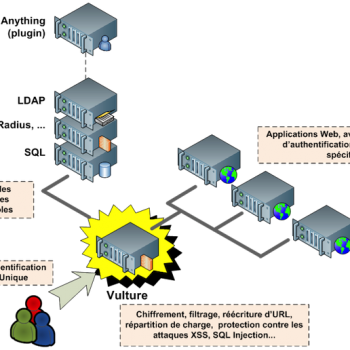
Let us acknowledge the definition of SQL injection attacks before indulging into the matter. Well, the SQL injection attack can be defined as the code injection technique, which is used to attack the applications that